Have you ever wondered how cybercriminals infiltrate seemingly impenetrable networks and steal sensitive data? The answer often lies in vulnerabilities within Active Directory (AD), the backbone of many Windows-based infrastructures. This article delves into the fascinating world of pentesting AD, unraveling the techniques and tools used by security professionals to identify and exploit weaknesses in this critical component.

Image: www.poplabsec.com
For those unfamiliar with AD, it’s a central directory service that manages user accounts, computers, and resources in a Windows network. Think of it as the control center for your digital kingdom. Pentesting AD involves simulating malicious attacks to uncover security gaps and weaknesses, ultimately strengthening the network’s defenses against potential threats. This proactive approach is crucial in today’s cyber landscape, where adversaries are constantly evolving their tactics.
Understanding the Active Directory Landscape
Before venturing into the world of AD pentesting, it’s essential to grasp the core components and functions of this powerful directory service. AD is comprised of various elements, each playing a vital role in managing user identities and network resources.
Key Components of Active Directory:
- Domain Controllers (DCs): These servers act as the central authority in an AD environment, storing user and computer accounts, group policies, and other vital information. They authenticate users and enforce access controls across the network.
- Domain Users: These represent individual users with varying levels of access privileges. Each user account is linked to a specific domain, granting them specific permissions within that domain.
- Groups: AD allows users to be grouped together, simplifying access management and policy enforcement. Grouping users based on roles or departments streamlines security policies and ensures efficient resource allocation.
- Organizational Units (OUs): OUs act as containers within a domain, enabling administrators to organize and manage users, computers, and groups in a hierarchical structure. This compartmentalization enhances administrative efficiency and facilitates targeted security policies.
The Pentesting Methodology: A Step-by-Step Approach
Pentesting AD requires a systematic approach, carefully traversing the network landscape to uncover vulnerabilities and potential attack vectors. A typical AD pentesting process often follows these key steps:
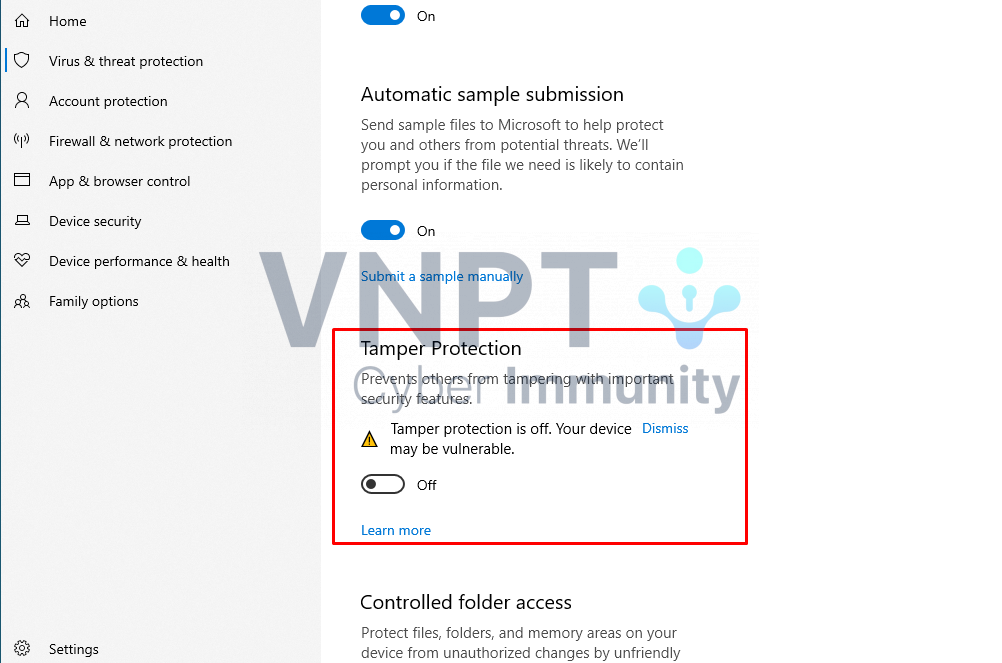
Image: sec.vnpt.vn
1. Reconnaissance: Gathering Intelligence
The reconnaissance phase is crucial for gathering information about the target network and its AD infrastructure. This stage involves:
- Network Scanning: Identifying active devices and services on the network, including domain controllers and other critical servers.
- Port Scanning: Detecting open ports and services running on discovered devices, revealing potential entry points for attackers.
- DNS Enumeration: Gathering information about DNS servers, domains, and subdomains, potentially uncovering domain name vulnerabilities.
- Active Directory Enumeration: Exploiting tools like LDAP (Lightweight Directory Access Protocol) to gather information about users, groups, and organizational units within the AD environment. This can reveal valuable insights about the network’s structure and potentially uncover weaknesses.
2. Vulnerability Assessment: Identifying Weaknesses
Once the initial reconnaissance phase is complete, the next step involves identifying potential vulnerabilities that could be exploited by attackers. This stage utilizes tools and techniques to uncover security flaws, including:
- Exploiting Known Vulnerabilities: Leveraging publicly known vulnerabilities in AD components and protocols to gain unauthorized access. This might involve utilizing exploits for common vulnerabilities like CVE-2020-1472 (ZeroLogon) or CVE-2021-21974.
- Password Cracking: Attempting to crack weak passwords through brute force attacks or dictionary attacks. This can be facilitated by tools like Hydra or Hashcat. Understanding password complexity policies and enforcing strong password requirements is crucial to mitigate this threat.
- Privilege Escalation: Gaining access to higher-privilege accounts, such as domain administrator accounts, by exploiting vulnerabilities or weak authentication mechanisms. This enables attackers to gain control over the entire network.
3. Exploitation: Demonstrating the Threat
The exploitation phase involves actually exploiting identified vulnerabilities to demonstrate the potential impact of successful attacks. This could involve:
- Data Exfiltration: Accessing and extracting sensitive data from the network, including user credentials, financial records, or proprietary information. Techniques like lateral movement and domain credential harvesting are often employed in this phase.
- Malware Deployment: Installing malicious software, such as ransomware or backdoors, on compromised systems to gain persistent access or disrupt network operations. Attackers might leverage techniques like PowerShell scripts or exploiting software vulnerabilities.
- Denial of Service (DoS) Attacks: Overloading services or systems with traffic, causing them to become unavailable to legitimate users. This could involve targeting domain controllers or other critical systems, disrupting operations and causing significant outages.
4. Reporting and Remediation: Closing the Gaps
Following a successful pentest, a comprehensive report should be provided to the client, detailing discovered vulnerabilities, potential attack vectors, and recommendations for remediation. This crucial step helps organizations understand the severity of the identified weaknesses and prioritize security fixes.
Tools of the Trade: Navigating the Pentesting Arsenal
Successful AD pentesting relies on a diverse set of tools, each catering to specific tasks and objectives. Here are some commonly used tools in the pentesting arsenal:
Core Tools:
- LDAP Browser: Tools like LDAPAdmin or Apache Directory Studio provide a graphical interface for exploring and querying AD directories, enabling reconnaissance and vulnerability assessment.
- Network Scanners: Tools like Nmap or Nessus are indispensable for identifying active hosts on the network, discovering open ports, and pinpointing potential vulnerabilities. These tools streamline the network reconnaissance phase, providing valuable insights into the target infrastructure.
- Password Cracking Tools: Tools like Hydra or Hashcat are used for attempting to crack passwords using brute force or dictionary attacks. Understanding the limitations and ethical considerations of password cracking is crucial.
- Exploitation Frameworks: Frameworks like Metasploit or Core Impact offer a collection of readily available exploits for exploiting known vulnerabilities in AD and other systems. These frameworks streamline the exploitation phase, facilitating the rapid identification and exploitation of identified vulnerabilities.
Evolving Threat Landscape: The Challenges of Modern AD Pentesting
The threat landscape surrounding AD is constantly evolving, as attackers continuously refine their techniques to bypass security measures and exploit new vulnerabilities. Here are some emerging trends in AD pentesting:
1. Advanced Persistence Threats (APTs):
APTs are sophisticated and targeted attacks designed to remain undetected within a network for extended periods, gathering sensitive data or preparing for future attacks. These attacks often utilize multi-stage techniques and exploit vulnerabilities in AD to establish persistent footholds in the network.
2. Insider Threats:
Insider threats, often originating from disgruntled employees or malicious actors with legitimate network access, pose a significant challenge. These attackers leverage their insider knowledge and privileges to compromise AD and gain control over sensitive data or resources.
3. Cloud Migration:
With the increasing adoption of cloud services, the hybrid IT landscape is becoming more complex. Pentesting hybrid AD environments requires adapting tools and techniques to encompass cloud-based components like Azure AD or AWS Directory Services, making the process more intricate.
Pentesting Active Directory And Windows-Based Infrastructure Epub
Conclusion: Protecting Your Active Directory Kingdom
Pentesting Active Directory is a crucial practice for understanding and mitigating vulnerabilities within your Windows-based infrastructure. By simulating attacker tactics and evaluating the network’s defenses, security professionals can proactively identify and remediate potential threats before they become real-world problems.
This comprehensive guide has provided a glimpse into the world of AD pentesting, covering key concepts, methodologies, and essential tools. Remember, staying vigilant and implementing robust security practices are paramount in the ever-evolving landscape of cyber threats. If you’re seeking further insights or want to delve deeper into specific aspects of AD pentesting, numerous online resources and specialized books are available.






